Google removed two malicious ad blockers, named AdBlock and uBlock, from Chrome Web Store after a researcher discovered that these extensions were carrying out an ad fraud scheme just to deceived Chrome users by using names of legitimate and popular blockers.
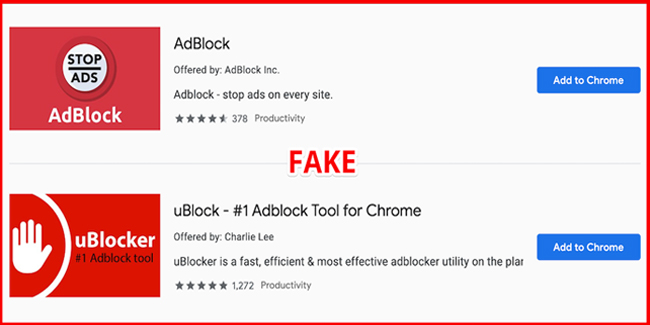
Andrey Meshkov, research and a maker of AdGuard, discovered that the extensions “AdBlock” and “uBlock” found in the store were fraudulent and alerted users in their blog post.
Though AdBlock and uBlock seem to be the legitimate extensions, these ad blockers may tend to do an ad fraud scheme to defraud affiliate marketing programs.
“This technique is known as Cookie stuffing, and this is basically an ad fraud scheme,” Meshkov said.
These two extensions in question, the AdBlock by AdBlock Inc. and uBlock by Charlie Lee, have names similar to these existing ad blockers AdBlock by getadblock and uBlock.org’s uBlock or Raymond Hill’s uBlock Origin. These fake extensions were based on the code of the original extensions.
In addition, these fake a blockers “both are based on the code of the original ‘AdBlock’ extension so the quality is good enough, according to Meshkov.
The researcher also found that AdBlock and uBlock hijacking cookie commissions from numerous sites such as Microsoft.com, Linkedin.com, Aliexpress.com, and Booking.com.
Meshkov recommends these tips on how to protect yourself from fake ad blockers.
- If you want to install a browser extension, think again.
- Don’t believe what you read in the extension’s description and reviews.
- Install extensions only from the trusted developers’ websites directly. Don’t just use the WebStore’s internal search.
Thank you for visiting our website. We hope we have helped you with regards to this matter. You may keep coming back for more informative guides.
READ ALSO | Cookie Stuffing: A Secret Blackhat Recipe for Cookies
